The KDM File Upload tab is where decryption keys (KDMs) are added into the TMS for distribution to the LMS and playback servers. It supports bulk uploads, drag-and-drop actions, and screen-targeted distribution for secure DCP playback.
🖥️ Interface Overview #
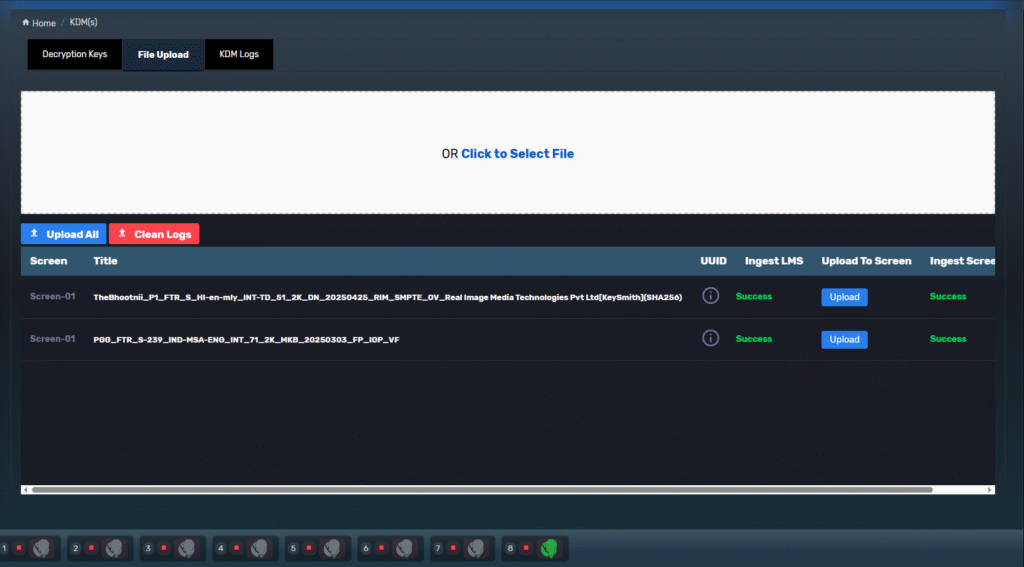
| Element | Description |
|---|---|
| Drag & Drop / File Select Area | Upload .xml KDM files by dragging them here or clicking to select |
| Upload All | Trigger LMS and Screen ingest for all files in queue |
| Clean Logs | Clears the upload history display (does not delete actual files) |
| UUID | Unique identifier of the KDM |
| Ingest LMS | Status of ingesting to central storage (LMS) |
| Upload to Screen | Retry button to push KDM to screen if it previously failed |
| Ingest Screen | Status of ingest into target screen’s server (IMB/DSP) |
📂 How It Works #
- Upload the File:
- Drag and drop
.xmlKDM files - Or click Click to Select File to browse locally
- Drag and drop
- Auto Detection:
- The TMS parses each file to identify which Screen it belongs to
- It will ingest to LMS first, then the corresponding Screen
- Retry Uploads:
- If screen was offline or projector IMB powered off, use the Upload button to retry
- Auto Push When Online:
- If a required KDM is already in LMS, it will automatically be pushed to the screen when it comes online and a scheduled session needs it
🔐 KDM Handling in TMS: Accepted vs. Blocked Types #
The TMS employs intelligent filtering to ensure only valid and compatible KDMs are ingested, thereby preventing playback issues caused by incompatible or redundant keys.
✅ Accepted KDMs #
SMPTE KDMs utilizing SHA-256 certificates are the industry standard for modern digital cinema systems. These KDMs are compatible with JPEG 2000 DCPs and are recommended for their enhanced security and compatibility.
Example Filename:
KDM_TelagaSuriramFinal_FTR_S-239_MSA-EN_MY_51_2K_FP_20250422_FP_SMPTE_VF@ims-xxx.cert.sha256.pem.kdm.xmlExample KDM’s that is accepted – Consist of cert.sha256
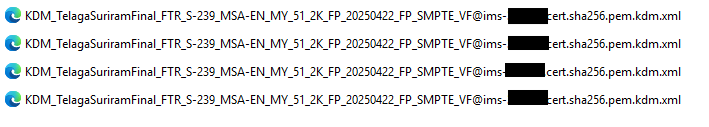
Key Characteristics:
- Conform to SMPTE ST 430-2 standards.
- Use SHA-256 hashing algorithms.
- Target specific IMBs (e.g.,
@ims-xxx). - Ensure secure and reliable playback.
⛔ Blocked KDMs #
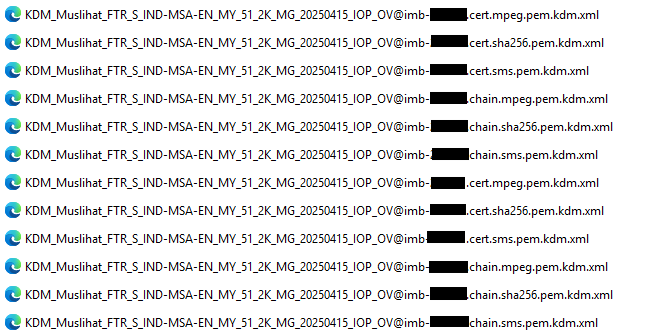
KDMs using SHA-1 (also referred to as MPEG or Interop KDMs) are considered obsolete and are automatically blocked by the TMS to prevent potential playback conflicts
Example Filenames:
...@imb-xxx.chain.mpeg.pem.kdm.xml
...@imb-xxx.chain.sms.pem.kdm.xml
...@imb-xxx.cert.sms.pem.kdm.xmlIn this example, the cert.sms , chain.mpeg, chain. sha256, chain.sms will be blocked by the TMS. It will accept the cert.mpeg and cert.sha256 KDM’s the rest will fail.
Reasons for Blocking:
- SHA-1 is now considered insecure and deprecated.
- MPEG/Interop KDMs are incompatible with modern JPEG 2000 DCPs.
- Ingesting multiple KDM types can cause conflicts within the IMB, leading to playback errors.
📊 KDM Compatibility Diagram #
The following diagram illustrates the compatibility of different KDM types with modern digital cinema systems:
+----------------------+----------------------+----------------------+
| KDM Type | Certificate Type | Compatibility |
+----------------------+----------------------+----------------------+
| SMPTE KDM | SHA-256 | ✅ Accepted |
| Interop KDM | SHA-1 (MPEG) | ❌ Blocked |
| SMS KDM | SMS Certificates | ❌ Blocked || SMPTE Chain KDM | SHA-256 Chain | ❌ Blocked || Interop Chain KDM |SHA-1 (MPEG)| ❌ Blocked || SMS Chain KDM | SMS Chain | ❌ Blocked |
+----------------------+----------------------+----------------------+
⚠️ Important Notes #
- SHA-256/SMPTE KDMs are used by all modern digital cinema servers.
- Avoid uploading SHA-1/MPEG/Interop KDMs to prevent playback issues.
- The TMS will automatically ingest valid KDMs into the LMS and attempt to distribute them to the appropriate screens.
- If a screen is offline or its IMB is powered off, the TMS will queue the KDM and automatically ingest it once the screen becomes available